PHOENIX - - The IRS, state tax agencies and the tax industry today warned tax professionals that account takeovers by cybercriminals are on the rise and practitioners increasingly are the targets.
Account takeovers occur when a thief manages to steal or guess the username and password of a tax professional, enabling access of their computers or their other online accounts. With these credentials, thieves can, for example, access a tax professional's IRS e-Services account to steal their Electronic Filing Identification Number (EFIN) or access tax pro software account to obtain critical taxpayer information.
"We urge tax professionals to be on the lookout for the warning signs of these schemes and many others that can contribute to data loss and identity theft," said IRS Commissioner John Koskinen. "A few simple steps can protect tax professionals as well as their clients."
Increasing awareness about account takeovers is part of the "Don't Take the Bait" campaign aimed at tax professionals. This is the second part of a special 10-week series aimed at increasing security awareness in the tax community. It is part of the Protect Your Clients; Protect Yourself effort. The IRS, state tax agencies and the tax industry, working together as the Security Summit, urge practitioners to learn to protect themselves from account takeovers.
Tax professionals and taxpayers are among a larger set of groups that face increased threats from account takeovers.
Javelin Strategy and Research conducts an annual identity fraud report. In 2017, it reported a surge in account takeover incidents nationwide – generally aimed at financial accounts – after years of decline. There was a 31 percent increase in the number of incidents for 2016 from 2015.
Account takeovers are a common source of data breaches of taxpayer data, leading to fraudulent tax filings for individuals and for businesses. Account takeovers are often the result of spear phishing emails specifically targeting the tax community. See last week's "Don't Take the Bait" news release for information about spear phishing.
Here's how account takeovers work: Thieves do their homework; perusing web sites and social media for clues about tax preparer's email addresses and business activities. Then, they pose as a familiar organization, for example, IRS e-Services or a private-sector tax pro software provider by sending a spear phishing email that appears similar to the IRS or the software provider. They may even pose as another tax professional, a familiar bank or, increasingly, a cloud-based storage provider.
Often, the email seems urgent with descriptions like: "Avoid Account Shutdown" or "Unlock Your Account Now." The email includes a disguised link that may take users to a page that looks like the login pages for IRS e-Services or a tax preparation software provider.
Alternatively, the email link or attachment may load malware onto computers to capture keystrokes, eventually giving the thieves access to user credentials when users log into their accounts. The thieves may pose as a potential client, emailing an attachment that claims to contain tax information but is really infected with keystroke logging malware. Here's an example of a fake IRS e-Services email:
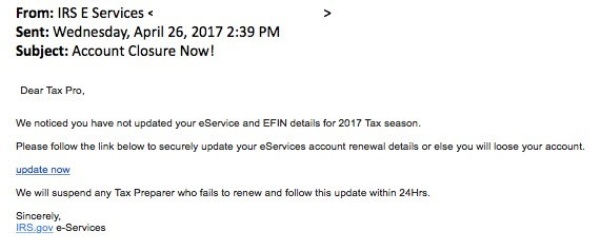
The email claims to be from "IRS E Services," slightly off from the official IRS e-Services name. Also, IRS e-Services does not send emails except through the Quick Alerts system. Note the "Account Closure Now!" subject line to instill urgency, as does the "update now" link.
Tax professionals should hover their cursors over a suspicious link to see the destination, which may be a URL like: bit.ly; ow.ly; or tinyurl.com, as opposed to an actual IRS.gov URL. The suspicious link takes the practitioner to a website designed to appear as the actual e-Services login page. Here's one example of a fake web page:
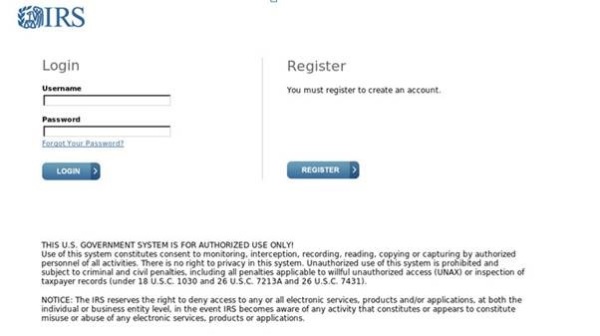
Once a thief obtains a tax pro's credentials, they immediately can access accounts and steal EFIN, which they can use either to file fraudulent tax returns or sell to other criminals who could file fraudulent tax returns. They may also use a Power of Attorney and Centralized Authorization File (CAF) number, allowing them to access clients' transcripts. Those who reuse usernames and passwords for multiple online accounts -- as many people do – may find the thief has accessed those accounts as well.
Protecting Clients and Businesses from Account Takeovers
Identity thieves have many schemes to steal login credentials. A common tactic is to use a spear phishing email that targets tax professionals. Here are a few steps to protect clients and business accounts:
- Educate all employees about the dangers of spear phishing and account takeovers. It only takes one employee to open a link to give cybercriminals access the entire system.
- Use strong, unique passwords. Better yet, use a phrase instead of a word. Use different passwords for each account. Use a mix of letters, numbers and special characters. Longer is better, but a minimum of eight to 10 characters. Use a password manager if necessary to help remember these unique credentials.
- Use the strongest encryption software available. Encrypt and password protect all sensitive data, using unique passwords for each document.
- Use strong malware/phishing software protection. Good software can help detect and stop malware or warn users when they are going to a suspected phishing site. A periodic deep scan also may help uncover embedded malware lurking in systems.
- Use two-factor authentication whenever possible – This practice helps protect accounts by requiring two steps for access. For example, the IRS Secure Access process requires credentials (username and password) plus a security code that is sent as a text to a mobile phone that is registered with the IRS. Account takeovers are one reason the IRS is moving to protect e-Services with this more rigorous process. Many banks and social media outlets are moving to two-factor authentication, either by using a code sent to an email address or phone. Use the two-factor option whenever possible.
- Check EFIN counts weekly. Access the application via e-Services and select "Check EFIN Status." If someone is using the EFIN without your knowledge, a higher number of returns filed under that number will result. Call the Help Desk immediately.
- Report phishing emails. Fraudulent phishing or malicious email can be sent to phishing@irs.gov. For more information, see Report Phishing.
- Report security incidents. The IRS considers these examples to be security incidents: a user clicked on a phishing link and entered their email credentials; a user clicked on a malicious URL that infected the computer; or someone created a domain like the user's domain and used that to send phishing emails to other preparers. Publication 4557, Safeguarding Taxpayer Data, provides guidance to report incidents. If the incident was an IRS-related scam, report it to the Treasury Inspector General for Tax Administration (TIGTA).


